By José Carlos Palma* In the shadowy realm of cyber espionage, few adversaries loom as ominously as ScarCruft, a sophisticated threat group with ties to North Korea. Known for its clandestine operations and advanced tactics, ScarCruft has emerged as a formidable force in the realm of state-sponsored cyber threats. Let’s
- April 16, 2024
Cybersecurity Experts Expose Vulnerabilities in Tesla’s Digital Key System By James Mitchell* In a startling demonstration of cyber vulnerability, cybersecurity researchers Tommy Mysk and Talal Haj Bakry from Mysk, a tech firm, have revealed how a Tesla Model 3 can be compromised using inexpensive hardware and social engineering tactics. Their
- March 25, 2024
By The Smartencyclopedia Staff & Agencies In a landscape where 5G coverage remains uneven, conversations about the imminent arrival of 6G are already taking the spotlight. OPPO, the global technology company, has shared its vision for Artificial Intelligence (AI) and 6G through two newly released white papers: the 2023 OPPO
- March 3, 2024
By José Carlos Palma* Introduction As the cloud becomes an integral part of IT infrastructure, the security landscape evolves, presenting unique challenges, especially for Linux workloads. In this comprehensive guide, we explore the fundamentals of Linux security in the cloud, emerging threats, and best practices to safeguard your cloud-based infrastructure.
- February 23, 2024
By The Smartencyclopedia Staff Imagine a world where artificial intelligence (AI) doesn’t merely mimic life, but seamlessly integrates with it, weaving a new tapestry of possibilities. This isn’t science fiction; it’s the burgeoning field of “Artificial Intelligence for Real Biological” (AI4RB), pushing the boundaries of both disciplines and promising transformative
- February 22, 2024
By The Smartencyclopedia Staff In a move paralleling its crackdown on greenwashing, the US Securities and Exchange Commission (SEC) has issued a stern warning against AI washing, cautioning businesses against making misleading claims about their artificial intelligence (AI) capabilities. SEC Chair Gary Gensler emphasized that securities law explicitly prohibits deceptive
- February 14, 2024
photo: CEO Paul Gray displays the MK6 OBU (left) and RSU. (Photo: Cohda Wireless) By The Smartencyclopedia Staff Cohda Wireless, a global leader in vehicle-to-everything (V2X) technology, has achieved a significant milestone with the certification of its MK6 V2X solution by the US Federal Communications Commission (FCC). The certification allows
- January 5, 2024
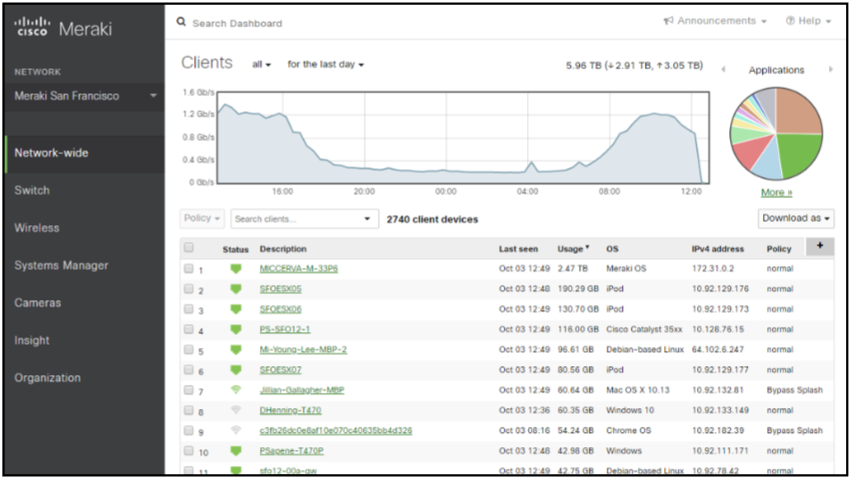
By José Carlos Palma* Dependency on Internet Connectivity Issue: Meraki’s cloud-based architecture relies heavily on internet connectivity. Network performance may be impacted during internet outages or disruptions. Solution: Implementing redundancy in internet connections and exploring failover options can mitigate the impact of internet issues on Meraki networking. Subscription Costs and
- January 3, 2024
By José Carlos Palma* In today’s dynamic and ever-evolving business landscape, organizations are increasingly seeking innovative and scalable solutions to streamline their IT infrastructure and enhance network security. One such solution that has gained prominence is Meraki cloud networking. This comprehensive suite of cloud-managed networking solutions offers businesses worldwide a
- January 3, 2024
By The Smartencyclopedia Staff In the rapidly evolving landscape of technology, artificial intelligence (AI) has played a pivotal role, shaping various sectors and posing both opportunities and challenges. Here are five ways AI, particularly exemplified by OpenAI’s ChatGPT chatbot, has been transforming our world: 1. ChatGPT Sparks a Tech Race
- January 1, 2024
By Smartencyclopedia Staff & Agencies In a landmark move, European Union member states and lawmakers reached a historic agreement on Friday, finalizing rules to regulate artificial intelligence (AI) models, including notable platforms like ChatGPT. The negotiations in Brussels lasted for 36 hours, resulting in a comprehensive framework for the ethical
- December 9, 2023
By José Carlos Palma* In 2019, the esteemed Henry Kissinger, a towering figure in American diplomatic history, issued a stark warning about the increasing reliance on artificial intelligence (AI) in the control of nuclear weapons. His concerns, rooted in a lifetime of experiences spanning the harrowing days of Nazi Germany
- November 30, 2023